The OSI (Open Systems Interconnection) seven-layer model serves as a conceptual framework for understanding how different computing systems interact over a network. It breaks down the communication process into seven distinct layers, with each layer handling specific tasks. Here’s a detailed overview of the OSI model, including an explanation of each layer, its functions, and its role in facilitating communication within networked systems.
Introduction
The OSI model was created by the International Organization for Standardization (ISO) to standardize and simplify network communications. It is commonly used to explain how various components of a network interact and how data is transmitted. By breaking down the entire communication process into seven distinct layers, each with its own functions and responsibilities, the model offers a clear understanding of network architecture.
The Open Systems Interconnection (OSI) model serves as a framework for comprehending data communications between any two connected systems. It breaks down the communication processes into seven distinct layers. Each layer has specific functions that support the layers above it while providing services to the layers below. The three lowest layers concentrate on transmitting traffic through the network to reach an end system, while the top four layers are involved in the end system to finalize the communication process.
A networking model provides a general way to divide computer networking functions into several layers. Each layer depends on the layers beneath it for support and, in turn, offers assistance to the layers above. This layered approach is often referred to as a “protocol stack” or “protocol suite.” Protocols, which are sets of rules, can function in hardware, software, or, as is common with many protocol stacks, a combination of both. Typically, the lower layers operate in hardware or firmware (software designed to run on specific hardware chips), while the upper layers function in software. The Open System Interconnection model is a seven-layer framework that outlines the requirements for communication between two computers. This model was defined by the ISO (International Organization for Standardization) standard 7498-1. It enables all network components to work together, regardless of the origin of the protocols or the computer vendor that supports them.
The main benefits of the OSI model
- Helps users understand the big picture of networking
- Helps users understand how hardware and software elements function together
- Makes troubleshooting easier by separating networks into manageable pieces
- Defines terms that networking professionals can use to compare basic functional relationships on different networks
- Helps users understand new technologies as they are developed
- Aids in interpreting vendor explanations of product functionality
The seven layers of the OSI model
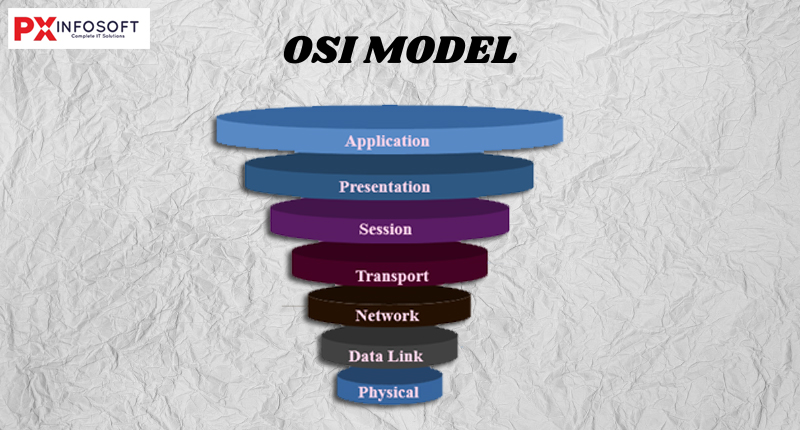
- Physical Layer
- Data Link Layer
- Network Layer
- Transport Layer
- Session Layer
- Presentation Layer
- Application Layer
Physical Layer
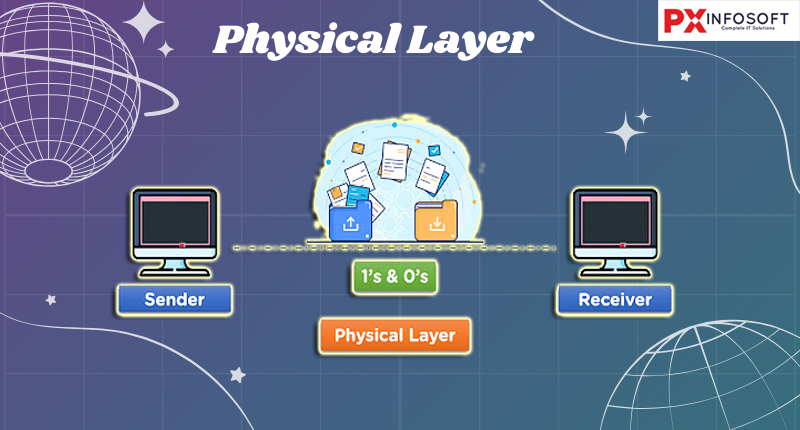
The physical layer of the OSI model outlines the specifications for connectors and interfaces, along with the requirements for the medium (cable). It includes electrical, mechanical, functional, and procedural details necessary for transmitting a bit stream over a computer network.
The Physical Layer is the foundational layer of the OSI model. Its main role is to handle the transmission and reception of raw data bits across a physical medium. This encompasses all the physical connections between devices that facilitate data transfer through cables, fiber optics, wireless signals, and more.
Key Functions
- Bit Transmission: It converts data into signals (electrical, light, or radio) for transmission through physical media.
- Physical Medium: Specifies the type of cables, connectors, and signaling mechanisms used to transmit data, such as twisted pair cables, coaxial cables, fiber optics, and wireless technologies.
- Data Rate Control: Controls the data transfer rate, ensuring that devices send and receive data at an acceptable speed.
- Signal Encoding and Decoding: It is responsible for encoding the data into a format suitable for transmission and decoding received signals.
Examples of Devices:
- Cabling system components
- Adapters that connect media to physical interfaces
- Connector design and pin assignments
- Hub, repeater, and patch panel specifications
- Wireless system components
- Parallel SCSI (Small Computer System Interface)
- Network Interface Card (NIC)
In a LAN environment, Category 5e UTP (Unshielded Twisted Pair) cable is generally used for the physical layer
for individual device connections. Fiber optic cabling is often used for the physical layer in a vertical or riser
backbone link. The IEEE, EIA/TIA, ANSI, and other similar standards bodies developed standards for this layer.
Data Link Layer
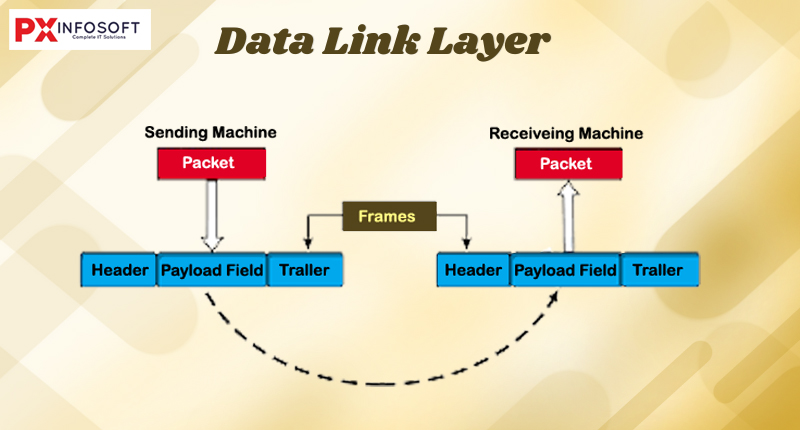
The Data Link Layer is the second layer of the OSI model. Its main role is to establish a reliable connection between two directly connected nodes, such as computers, switches, and routers. This layer manages error detection and correction while also organizing data into frames.
Key Functions:
- Framing: The Physical Layer divides the stream of bits into manageable data units known as frames. Each frame includes control information, such as addresses and error-checking data, to guarantee accurate delivery. Additionally, it employs error detection and correction methods, like checksums and cyclic redundancy checks (CRC), to identify and fix any errors that may arise during transmission.
- Flow Control: Manages the flow of data to prevent congestion and ensures that data is transferred at an appropriate speed.
- Media Access Control: Determines how devices access the shared transmission medium (such as Ethernet or Wi-Fi), avoiding collisions in data transmission.
- Allows a device to access: The network to send and receive messages.
- Offers a physical address: So a device’s data can be sent on the network.
- Works with a device’s networking software: When sending and receiving messages
- Provides error-detection capability
Examples of Protocols:
- Ethernet: For local area networks (LANs).
- Wi-Fi (IEEE 802.11): For wireless networks.
- PPP (Point-to-Point Protocol): For serial communication links.
Common networking components
- Network interface cards
- Ethernet and Token Ring switches
- Bridges
NICs have a layer 2 or MAC address. A switch uses this address to filter and forward traffic, helping relieve
congestion and collisions on a network segment. Bridges and switches function in a similar fashion; however, bridging is normally a software program on a CPU, while switches use Application-Specific Integrated Circuits (ASICs) to perform the task in dedicated hardware, which is much faster.
Network Layer
The Network Layer is the third layer of the OSI model. It is responsible for routing data from the source to the destination across different networks, ensuring that data can traverse multiple networks and reach the correct endpoint.
Layer 3, known as the network layer in the OSI model, establishes a logical addressing system that allows data packets to be routed through various layer 2 networks like Ethernet, Token Ring, and Frame Relay. It’s important to note that addresses at the network layer are often called logical addresses. In the beginning, companies like Novell created their own proprietary addressing systems for layer 3. However, as the networking industry has progressed, the need for a standardized layer 3 addressing system has become clear. The Internet Protocol (IP) addresses simplify the process of setting up networks and connecting them with each other. The Internet relies on IP addressing to enable connectivity among millions of networks globally.
To manage the network more effectively and control packet flow, many organizations divide their network layer addressing into smaller segments called subnets. Routers utilize the network or subnet part of the IP address to direct traffic between different networks. Each router needs to be specifically configured for the networks or subnets connected to its interfaces. Routers communicate with each other through routing protocols like Routing Information Protocol (RIP) and Open Shortest Path First (OSPF) to discover other networks and determine the best routes to reach them based on various criteria, such as the path with the fewest routers. These routing decisions are made at the network layer by routers and other connected systems.
When transmitting packets across various networks, it may be necessary to modify their outbound size to align with the layer 2 protocol in use. This adjustment is achieved through a process called fragmentation, typically handled by the network layer of a router. The reassembly of fragmented packets occurs at the network layer of the destination system.
The network layer also plays a role in diagnostics and reporting any logical discrepancies in standard network operations. When a networked system detects a variation, it can initiate diagnostics and will report the issue back to the original sender of the packet that deviates from normal operations. However, there is an exception for content validation calculations. If the receiving system’s calculation does not align with the value sent by the originating system, the receiver will discard the packet without notifying the sender. The responsibility for retransmission falls to a higher layer’s protocol. Additionally, some basic security measures can be implemented by filtering traffic based on layer 3 addressing on routers or similar devices.
Key Functions:
- Routing: Determines the best path for data to travel from the source to the destination across a network or set of interconnected networks.
- Logical Addressing: Uses logical addresses such as IP (Internet Protocol) addresses to identify devices across networks and facilitate the correct routing of data.
- Packet Forwarding: Breaks data into packets and forwards them to their next destination, according to routing protocols and tables.
- Fragmentation and Reassembly: Divides large packets into smaller units if necessary, and reassembles them at the destination.
Examples of Protocols:
- IP (Internet Protocol): Defines addressing and routing methods.
- ICMP (Internet Control Message Protocol): Used for diagnostic purposes like ping and traceroute.
- ARP (Address Resolution Protocol): Resolves IP addresses to MAC addresses.
- Routers operate at the Network Layer, enabling communication between different networks, such as between a home network and the internet.
Transport Layer
The Transport Layer is the fourth layer of the OSI model. Its main role is to ensure that data is delivered reliably and efficiently from the source to the destination devices, no matter what the underlying network infrastructure is. The transport layer of the OSI model provides end-to-end communication between devices across a network. Depending on the application, this layer can offer either reliable, connection-oriented communication or connectionless, best-effort services.
Key Functions:
- Segmentation and Reassembly: Divides large messages into smaller segments and reassembles them at the destination.
- Reliability and Error Control: Provides mechanisms for reliable data transfer, ensuring that data is delivered without errors and in the correct sequence. This is done using acknowledgment signals and retransmission requests in case of errors.
- Flow Control: Manages the rate of data transmission to prevent congestion and ensure that the receiving device is not overwhelmed.
- Connection Management: Establishes, maintains, and terminates communication sessions between devices, ensuring that both ends of the communication are synchronized.
Examples of Protocols:
- TCP (Transmission Control Protocol): Provides reliable, connection-oriented communication, ensuring data is received in order and without loss.
- UDP (User Datagram Protocol): Provides connectionless communication, where reliability is not guaranteed, but it is faster than TCP.
Some of the functions offered by the transport layer include:
- Application identification
- Client-side entity identification
- Confirmation that the entire message arrived intact
- Segmentation of data for network transport
- Control of data flow to prevent memory overruns
- Establishment and maintenance of both ends of virtual circuits
- Transmission-error detection
- Realignment of segmented data in the correct order on the receiving side
- Multiplexing or sharing of multiple sessions over a single physical link
Devices that operate at the Transport Layer include hosts and end devices, such as computers, servers, and routers, where data is segmented into transportable units for end-to-end delivery. The most common transport layer protocols are the connection-oriented TCP Transmission Control Protocol (TCP) and the connectionless UDP User Datagram Protocol (UDP).
Session Layer
The Session Layer is the fifth layer of the OSI model. It manages sessions or connections between applications. This layer establishes, manages, and terminates sessions between communicating systems. The session layer, provides various services, including tracking the number of bytes that each end of the session has acknowledged receiving from the other end of the session. This session layer allows applications functioning on devices to establish, manage, and terminate a dialog through a network.
Key Functions:
- Session Establishment: Establishes, maintains, and terminates communication sessions between applications. A session is a logical connection between two devices that allows them to exchange data.
- Synchronization: Ensures that data transfer is properly synchronized between the sender and the receiver, managing the exchange of data in the form of requests and responses.
- Dialog Control: Manages the flow of data between two devices by ensuring that the communication can be half-duplex (one-way at a time) or full-duplex (both-way simultaneously).
Examples of Protocols:
- RPC (Remote Procedure Call): Allows programs to request services from programs running on other machines.
- NetBIOS: Provides services related to file and printer sharing on Windows networks.
Session layer functionality
- Virtual connection between application entities
- Synchronization of data flow
- Creation of dialog units
- Connection parameter negotiations
- Partitioning of services into functional groups
- Acknowledgements of data received during a session
- Retransmission of data if it is not received by a device
Presentation Layer
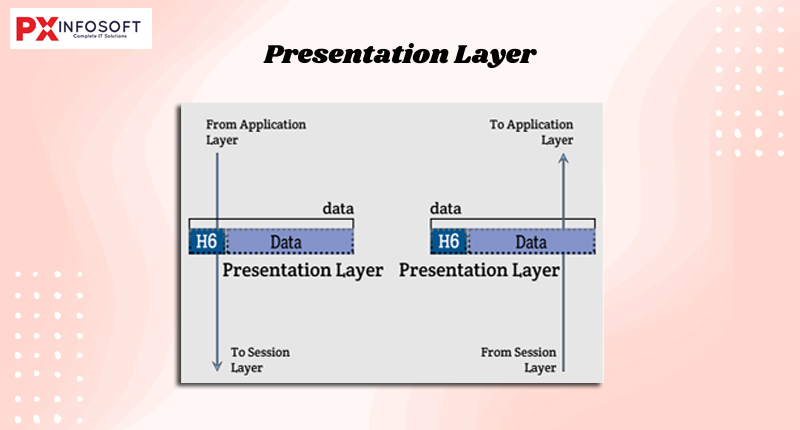
The Presentation Layer is the sixth layer of the OSI model. It is responsible for translating the data between the application layer and the transport layer, ensuring that the data is in a readable format for the receiving application. The presentation layer, is responsible for how an application formats the data to be sent out onto the
network. The presentation layer basically allows an application to read (or understand) the message.
Key Functions:
- Data Translation: Converts data from the format used by the application into a standard format that can be understood by the recipient’s system. It is responsible for the conversion between different data formats (e.g., EBCDIC to ASCII).
- Encryption and Decryption: Ensures data security by encrypting data before transmission and decrypting it at the receiving end.
- Data Compression: Compresses data to reduce the amount of bandwidth required for transmission and decompression on receipt.
Examples of Protocols:
- SSL/TLS: Protocols used for encrypting data in transit.
- JPEG, GIF, PNG: Image file formats used for data encoding and decoding.
Presentation layer functionality
- Encryption and decryption of a message for security
- Compression and expansion of a message so that it travels efficiently
- Graphics formatting
- Content translation
- System-specific translation
This layer essentially ensures that data is properly formatted and secure for application use.
Application Layer
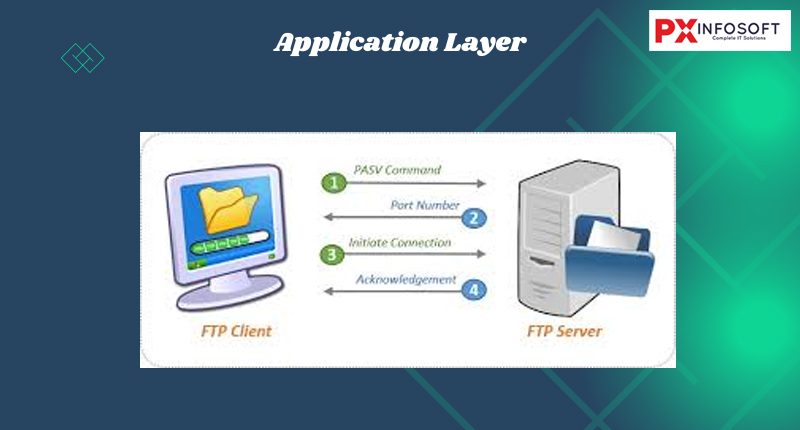
The Application Layer is the seventh and topmost layer of the OSI model. It directly interacts with end-user applications, providing network services such as file transfer, email, and web browsing. This layer enables communication between applications across a network.
Key Functions:
- Network Services: Provides services that allow applications to interact with the network, such as file transfer, email, and remote login.
- User Interface: Allows applications to interface with the user, presenting data in a user-friendly format.
- Application Protocols: Defines rules for communication between software applications, ensuring that both the client and server can exchange data effectively.
Examples of Protocols:
- HTTP (HyperText Transfer Protocol): Used for web browsing.
- FTP (File Transfer Protocol): Used for file transfers.
- SMTP (Simple Mail Transfer Protocol): Used for sending email.
Application layer functionality
- Support for file transfers
- Ability to print on a network
- Electronic mail
- Electronic messaging
- Browsing the World Wide Web
The Application Layer is where users typically interact with networked services, such as accessing a website or sending an email.
Conclusion
The OSI model serves as a helpful framework for grasping how networks interact and ensuring reliable and efficient data transmission between devices. Each layer of the OSI model is essential for successful communication between systems, starting from the physical transmission at the Physical Layer to the application-level interactions at the Application Layer. Although the OSI model is a theoretical construct, it continues to be a valuable resource for network design, troubleshooting, and protocol development. In real-world applications, the OSI model is frequently compared to the TCP/IP model, which is more prevalent in contemporary networking. Nonetheless, the OSI model remains crucial for understanding the structure and flow of network communications.