In today’s digital landscape, ensuring security is essential. Whether you’re surfing the internet, making online purchases, or managing sensitive information, protecting your personal data is vital. One key technology that helps secure online communications is SSL (Secure Sockets Layer). But what is SSL, and how does it function? In this guide, we will delve into the definition of SSL, its development over time, its operational mechanics, the various types of SSL certificates available, and the importance of SSL for both website owners and their visitors.
What is SSL?
SSL is the widely used security protocol that underpins nearly all secure Internet transactions. In essence, SSL converts a standard reliable transport protocol, like TCP, into a secure communication channel that is ideal for handling sensitive transactions. The SSL protocol outlines the procedures for establishing a secure communications channel, but it does not specify which cryptographic algorithms should be employed. SSL accommodates a variety of algorithms and acts as a framework that allows for the convenient and distributed use of cryptography.
Originally developed by Netscape Communications to enable secure connections between browsers and web servers, Secure Sockets Layer (SSL) has become the standard for web security. The first version of SSL was never released due to issues with protecting credit card transactions online. In 1994, Netscape introduced SSLv2, which allowed for the confidentiality of credit card numbers and authenticated web servers through encryption and digital certificates. By 1995, Netscape enhanced the cryptographic algorithms and addressed many security issues present in SSLv2 with the launch of SSLv3, which supports a wider range of security algorithms than its predecessor.
Uses for SSL
The applications for SSL are numerous. Any service that requires data transmission over an unsecured network, like the Internet or a corporate intranet, could benefit from SSL. It offers security and, perhaps more importantly, peace of mind. With SSL in place, you can feel confident that your data is protected from eavesdropping and tampering.
SSL is a relatively recent addition to the embedded world, primarily because traditional embedded systems microprocessors have struggled with its complexity. However, with the introduction of Rev. A of the Rabbit 3000 microprocessor, hardware support has been implemented to accelerate some of the more intricate SSL cryptography tasks. This advancement makes SSL a practical option in a market where standard security protocols, which are often complicated, have not been widely adopted. The potential applications for embedded SSL are as diverse as those found in the PC realm. Here are just a few examples of possible uses for embedded SSL.
- The Internet-enabled vending machine can now become a reality.
- Home automation systems can be Internet-enabled.
- Readings from medical devices can be sent over a standard network.
- Make a telephone switch Web-configurable.
- Remote-entry configuration.
History and Evolution of SSL and TLS
The original Secure Sockets Layer (SSL) was created in the early 1990s by Netscape Communications Corporation to secure HTTP, a protocol that transmits data in plain text over the Internet. The first official version released was 2.0, which became widely accepted even though it had some design issues with the protocol.
In the late 1990s, it became clear that SSL 2.0 was not secure. As a result, Netscape started developing SSL 3.0. Alongside Netscape, the Internet Engineering Task Force (IETF), which oversees internet standards, began working on standardizing SSL, leading to the creation of TLS (Transport Layer Security). Although SSL 3.0 was released sooner and quickly became the industry standard, it was not developed with the same rigor as TLS. TLS was finalized in 2000, marking the introduction of the first standardized protocol for SSL. While SSL 3.0 is still commonly used, it is largely considered obsolete for new development, as nearly all modern browsers now support TLS.
How Does SSL Work?
SSL operates by utilizing a mix of encryption, hashing, and certificate-based authentication to establish a secure link between the server and the client. Here’s a straightforward explanation of how SSL/TLS encryption functions:
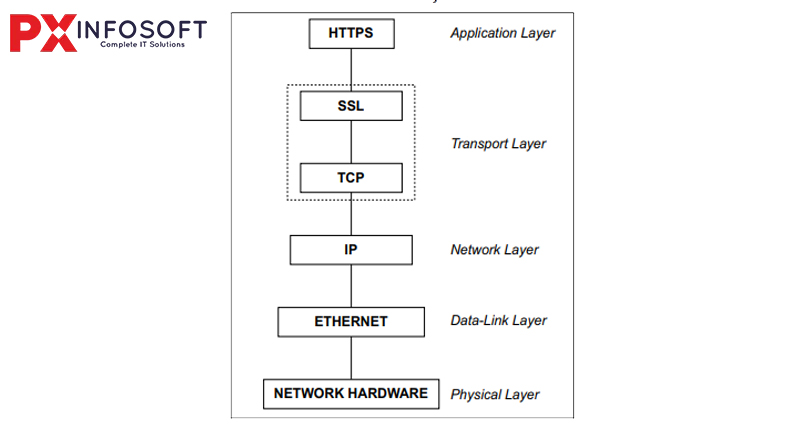
The SSL Handshake
In the establishment of a secure connection between a client (such as a web browser) and a service provider (like a website), a TLS handshake occurs. This secret exchange of greetings resembles a handshake between two individuals, but here, it serves as a way for them to agree on the information they wish to keep secure before sharing anything. This process includes reaching an agreement on the encryption methods they will use to communicate safely while verifying each other’s identities through encryption keys. Ensuring privacy, in addition to implementing safety measures for the information being transmitted, is also very important. This involves several steps:
- Client Hello: This is where the client starts the handshake process by sending a “hello” message to the server. This message includes the encryption methods it supports and other relevant parameters. The user’s browser (client) makes a request to the server, providing a list of supported encryption algorithms (ciphers) along with a randomly generated number.
- Server Hello: The server replies with a random number of its own, chooses a cipher that is compatible with both the client and server, and transmits its SSL certificate, which includes the server’s public key, to the browser. In return, the server sends a hello message where it selects an encryption method before providing its digital certificate for authentication.
- Authentication and Key Exchange: The browser checks the server’s certificate to ensure it comes from a trusted Certificate Authority (CA). If the certificate is valid, the client encrypts a new random number, known as the “pre-master secret,” using the server’s public key and sends it back to the server. At this point, both the client and server establish a shared symmetric key for encrypting and decrypting data during their session. This process may involve methods like Diffie-Hellman key exchange. To confirm its identity, the server provides a digital certificate, and it is the client’s responsibility to verify that the certificate is from a trusted source.
- Session Key Generation: The client and server utilize the pre-master secret along with the random numbers exchanged earlier to create a symmetric session key. This session key is essential for encrypting the remainder of the communication throughout the session.
- Secure Communication: Once the session key is established, the client and server can securely exchange data, ensuring that all transmitted information is encrypted with the session key. To verify that the handshake was successful and that encryption is properly set up, both parties send a ‘finished’ message.
Components of SSL
SSL certificates consist of a key pair: a public key and a private key. These keys collaborate to create a secure, encrypted connection. Additionally, the certificate includes the “subject,” which identifies the owner of the certificate or website. There are a few key components that make up the SSL/TLS protocol:
- Public and Private Keys: SSL employs asymmetric encryption, which involves two keys: a public key and a private key. The public key is used to encrypt the data, while only the matching private key can decrypt it. This process guarantees that sensitive information is transmitted securely. These keys are a connected pair of text files that are generated together when you create your Certificate Signing Request (CSR). SSL operates by sharing one key from the pair (the public key) with the outside world, while keeping the other key (the private key) confidential and known only to you.
- SSL Certificates: An SSL certificate is a digital document provided by a Certificate Authority (CA). It includes the public key, the domain name, details about the organization, and the expiration date. Additionally, SSL certificates feature a signature from the CA to verify the authenticity of the certificate. SSL certificates are essential for enabling websites to use HTTPS, providing a more secure connection than HTTP. An SSL certificate is a data file stored on a website’s origin server. These certificates facilitate SSL/TLS encryption and include the website’s public key, its identity, and other relevant information. When devices try to connect with the origin server, they refer to this file to access the public key and confirm the server’s identity. The private key, however, remains confidential and protected.
- Session Keys: After the SSL handshake is finished, symmetric encryption with session keys takes over. Session keys are quicker than asymmetric encryption and are utilized to encrypt and decrypt the data shared during the session. A session key is a randomly generated key used for encrypting and decrypting data, ensuring secure communication between a user and another computer or between two computers. These keys are often referred to as symmetric keys since the same key is utilized for both the encryption and decryption processes.
The Role of SSL in Online Security
SSL is essential for ensuring security on the internet today. Without it, web traffic could be easily intercepted and altered by unauthorized parties. Here’s how SSL enhances online security: SSL is a widely used technology that secures internet connections by encrypting the data exchanged between a website and a browser (or between two servers). This encryption stops hackers from accessing or stealing any information being transferred, including sensitive personal or financial details.
- A. Data Encryption : SSL encrypts all data sent between the server and the client, making it extremely difficult for anyone, including hackers, to access the information. The SSL protocol functions between the application layer and the TCP/IP layer, enabling it to encrypt the data stream itself for secure transmission using any application layer protocols. Various algorithms can be employed for data encryption and for generating the message authentication code. Some algorithms offer high security levels but demand significant computational resources for encryption and decryption. Conversely, other algorithms may be less secure but allow for faster encryption and decryption. The length of the encryption key plays a crucial role in determining security; generally, the longer the key, the more secure the data. SSL specifies cipher suites to outline the cryptographic algorithms utilized during an SSL connection.
SSL uses two encryption techniques:
- Public key cryptography standard (PKCS)
- A mutually agreed symmetric encryption technique, such as DES (data encryption standard)
- B. Authentication: SSL certificates serve to confirm the identity of a server. This verification process helps guarantee that users are interacting with the genuine website rather than a fraudulent imitation, such as phishing sites. Through SSL, authentication occurs via the exchange of certificates, which are data blocks formatted according to the ITU-T standard X. 509. These X. 509 certificates are issued and digitally signed by a recognized external authority known as a certificate authority.
- C. Integrity: SSL guarantees data integrity, ensuring that information remains unchanged and uncorrupted while being transmitted. If any alterations occur, SSL will identify the modification and end the connection. It safeguards the data you send and receive, keeping it intact during transmission. Data Encryption: SSL encrypts the information exchanged between the user’s browser and the server, shielding sensitive details like passwords, credit card numbers, and personal information from potential interception by hackers.
Types of SSL Certificates
There are several types of SSL certificates, each designed for different needs:
- Domain Validated (DV) Certificates: These are the most basic and cost-effective type of SSL certificate. They confirm only that the applicant owns the domain, without validating the identity of the organization. DV certificates are perfect for personal websites or blogs.
- Organization Validated (OV) Certificates: OV certificates offer more comprehensive validation, which includes verifying the identity of the organization. Businesses utilize these certificates to demonstrate their legitimacy to customers.
- Extended Validation (EV) Certificates: EV certificates provide the highest level of validation and security. They feature a green address bar in the browser and involve a thorough vetting process. Financial institutions and e-commerce websites frequently use EV certificates to build trust with their users.
- Wildcard Certificates: Wildcard SSL certificates provide security for a domain along with all its subdomains. For instance, a wildcard certificate for *.example.com will cover shop.example.com, blog.example.com, and others.
- Multi-Domain (SAN) Certificates: Multi-domain certificates allow organizations to secure multiple domains using just one certificate. This is particularly beneficial for those that manage several different domains and wish to streamline their SSL certificate management.
Benefits of SSL Certificates
It helps to prevent eavesdropping, impersonation, data theft, identity theft, and Man-in-the-middle attacks by encrypting all data in transit. Additionally, it lowers the risk of phishing attacks. It’s quite uncommon for fraudulent or scam websites created by attackers to obtain an OV or EV SSL certificate.
- Enhanced Security: SSL guarantees that sensitive information, such as login credentials and payment details, is transmitted securely and safeguarded against eavesdropping and tampering.
- Increased Trust: Websites that have SSL certificates show a padlock icon in the browser, signaling to users that their connection is secure. This fosters trust and confidence, particularly for e-commerce sites.
- SEO Benefits: Google has confirmed that having an SSL certificate is a factor in search engine rankings. Websites that use SSL may achieve higher positions in search results than those that do not.
- Compliance: SSL is essential for meeting compliance standards such as PCI-DSS (Payment Card Industry Data Security Standard) for managing payment information, as well as GDPR (General Data Protection Regulation) for safeguarding user data.
How to Implement SSL on Your Website
Acquire an SSL Certificate: Select the right type of SSL certificate that fits your requirements and buy it from a reputable Certificate Authority (CA). Set Up the SSL Certificate: Adhere to the installation instructions given by your hosting provider, which usually includes uploading the certificate files to your web server. Revise Website Links: Make sure that all internal links on your website are changed to use HTTPS instead of HTTP.